
- Crypto
- July 3, 2025
Cryptocurrency offers freedom, but comes with new risks that don’t always look suspicious at first. One of the lesser-known threats is a dusting attack. It starts quietly, with a tiny, random transaction in your wallet. Most users don’t even notice it, or if they do, they ignore it, but these small transactions can reveal much more than anyone can expect.
Dusting attacks don’t steal your funds outright. Instead, the scammers aim to trace your wallet’s activity. Sometimes, they even link it to your real identity. That’s what makes them such a problem in today’s digital world.
In this article, we will discuss what these attacks are, why they’re used, and what steps one can take to stay protected.
What Is a Crypto Dusting Attack?
A crypto dusting attack involves someone sending you a very small amount of cryptocurrency, usually just a few cents or even less. This small amount is called “dust.” It’s not enough to be useful, but it shows up in your wallet like any normal transaction.
You might ignore it, thinking it’s just an accidental transfer or some sort of bonus. But in reality, that dust might be the first step in a dangerous plan.
Once the dust hits your wallet, scammers start watching your activity. They track how and when you move your funds. If you ever use that dust as part of another transaction, even by accident, it helps them connect your wallet to others you own or interact with.
That small piece of data helps build a larger map of one’s crypto activity. And from there, the risks start to increase.
Why Do Scammers Use Dusting Attacks?

These attacks aren’t about stealing a few cents; they’re about surveillance, analysis, and setting up future scams.
- Tracking Wallet Movements
When someone sends dust to a person, they monitor their wallet to see how it responds. If the person spends their crypto and includes that dust amount in a new transaction, they can follow it across the blockchain. This helps them trace how funds flow between wallets.
By tracking those flows, scammers or even data analytics firms can link multiple wallets together. This reduces privacy and makes it easier for them to see how much crypto someone holds.
- Building a Profile
Not every wallet is worth targeting. So, scammers use dusting as a way to learn more about users. If they see someone frequently trading, holding large balances, or interacting with certain exchanges, they might flag their wallet as a potential target.
This is especially common before phishing attempts. Scammers prefer to go after users who look active or well-funded. Dusting helps them decide who to target and how to do it.
- Linking Wallets to Real Identities
While crypto is often called “anonymous,” it’s more accurate to say it’s “pseudonymous”. Your wallet address doesn’t show your name, but if someone can connect that address to an account on an exchange or NFT platform (especially ones that require ID verification), your identity could be exposed.
Dusting gives scammers the data they need to start that process. They follow one’s transactions until they hit a known address, then use that information to figure out who the person is.
How to Know If You’ve Been Dusted?
Dusting attacks don’t come with a warning. But there are a few things one can observe:
- Tiny Random Transactions Appear
If you check your wallet and see a small, unfamiliar transaction, especially one with no clear origin or purpose, it might be a dusting attempt. These transactions often involve amounts that are too small to use but still show up in your history.
Don’t assume it’s a reward or an airdrop. If it came from a random address unexpectedly, then it’s probably dust.
- You See Unusual Tokens
Some scammers send strange or fake tokens instead of real coins. These tokens might have names that sound official or completely random. They’re designed to catch people’s attention so that they click or interact with them.
Clicking or trading these fake tokens can trigger phishing sites or malicious contracts. Even just viewing them in certain wallets could expose one to risks.
- Your Wallet’s Activity Feels Off
Even if the dust transaction didn’t trigger an alert, you might notice that your wallet has a new transaction that doesn't line up with anything you did. If the transaction was too small to be useful and came from an unknown address, it’s worth treating it as a potential dusting attack.
Risks of Ignoring Dusting Attacks
People often ignore that tiny transaction and carry on as usual. But doing nothing can backfire.
- One Can Lose Their Privacy: Once the dust is in someone’s wallet, scammers will start watching. If they later send a transaction that includes that dust, even without realizing it, it tells them which other addresses are connected to them. This weakens the privacy and can expose patterns in how someone is using their crypto. Even wallets that are “cold” or rarely used become part of the picture if they get linked through one transaction.
- People can be targeted later: A common follow-up to dusting is phishing. Scammers might use what they learned to send fake emails to their targets that look like they’re from their exchange. Or they might message with fake support offers pretending to help with a “wallet error.” These scams are easier to pull off once the attacker has a basic idea of who the person is and what platforms they use. Dusting gives them that starting point.
- One Could Be Part of a Larger Network Map: Sometimes, the attacker isn’t even after you specifically. They might be mapping hundreds of wallets to sell that data later, use it for blackmail, or exploit vulnerabilities in certain platforms. By ignoring the dust, you might unknowingly help build that bigger web and expose yourself to new risks down the road.
How to Protect Yourself From Dusting Attacks?
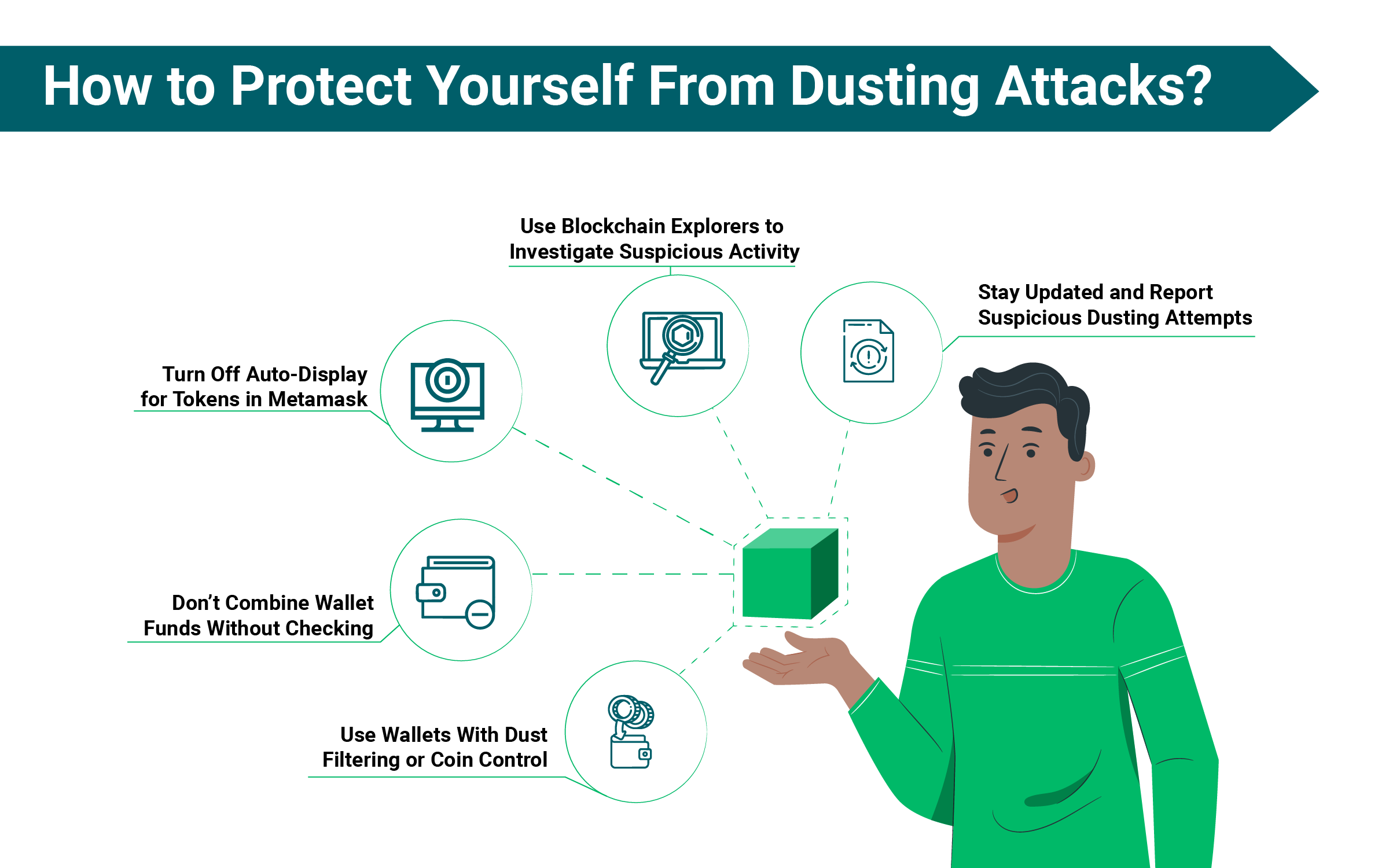
You can’t stop someone from sending you crypto. But you can control how you react to it and how you handle your wallet.
- Use Wallets With Dust Filtering or Coin Control
Some advanced wallets like Samourai or Wasabi automatically detect and hide dust amounts. They also let you choose which coins or UTXOs to include in a transaction. This means one can avoid ever spending dust by accident.
If you’re using a basic wallet, you may not have these features. But even just being aware of what dust looks like can help one to avoid it and safeguard oneself.
- Don’t Combine Wallet Funds Without Checking
If you receive dust in one wallet, avoid sending all your funds in one transaction. Doing so could link that dusted wallet to others that were previously private.
A better move is to keep wallets separate. Using one for trading, one for long-term holding, and one for interactions with DeFi or NFTs can help minimize risks. That way, if one gets dusted, it doesn’t compromise your entire crypto presence.
- Turn Off Auto-Display for Tokens in Metamask
Metamask and other popular wallets often show tokens automatically. This is convenient, but risky. Some scammers use fake tokens to bait users into clicking on them.
Turning off auto-display makes sure one only sees tokens they’ve added manually. This simple setting can prevent one from falling into a trap.
- Use Blockchain Explorers to Investigate Suspicious Activity
If you see an unknown token or a very small transaction, check it on a blockchain explorer like Etherscan or Blockstream.info. These tools can show if the token is linked to known scams or if the dust came from a suspicious address. This helps you make informed decisions before interacting with anything in your wallet.
- Stay Updated and Report Suspicious Dusting Attempts
Dusting attacks may be indicative of more sophisticated tracking or phishing plots. In case you encounter suspicious activity, report it on channels such as Chainabuse, your wallet provider, or the corresponding cybercrime authorities. While not all incidents lead to loss, reporting helps expose patterns and warn others.
You can also explore security-focused blogs and scam prevention platforms that track dusting trends and provide response tips. Also, scam recovery services like financial recovery experts offer resources for identifying dusting attempts and learning how to react safely.
What to Do If You Notice a Dust Attack?
If you suspect you’ve been dusted, don’t panic. But don’t ignore it either.
- Don’t Interact With the Dust
Avoid touching dust and don’t try to return it. Don’t send it to a friend or include it in a transaction. Interacting with it gives the attacker more data and confirms that your wallet is active. Even just one careless transaction can connect your wallet to others you’ve used.
- Move Your Main Funds to a Clean Wallet
If you’re worried about privacy or security, create a new wallet and send your funds there, without including the dust. Make sure to double-check the amount and leave out any tokens or UTXOs you didn’t add yourself.
This gives you a clean slate and keeps the dusted wallet isolated. It’s a simple way to break the trail scammers are trying to follow.
- Watch for Phishing or Social Engineering
After a dusting attack, scammers often try to reach out through email, Telegram, or even fake support tickets. They might mention recent transactions to make their messages seem legit.
Stay alert and never click on links you weren’t expecting. Always go directly to the official website if you need support. If someone contacts you first, assume it’s fake.
- Monitor Your Wallet and Future Transactions
Keep an eye on incoming transactions going forward. If you continue to see dust or odd activity, it may signal that your address is being watched or targeted.
Using a block explorer or a wallet that flags dust can help you stay aware and respond early.
Are Dusting Attacks Illegal or Just Annoying?
In most cases, dusting itself isn’t illegal. Sending a tiny amount of crypto doesn't violate any laws, particularly when blockchain networks are open and public, but that doesn't mean that it is harmless.
When dusting is used as a precursor to phishing, extortion, or identity theft, it is part of a much larger scam, and that’s when legal consequences come in.
It’s also worth noting that some data firms run dusting campaigns for research or marketing purposes. While that might not be “criminal,” it’s still invasive. And it shows just how valuable blockchain data has become to companies and scammers alike.
FAQs (Frequently Asked Questions)
A crypto dusting attack is when someone sends a tiny amount of cryptocurrency, often just a few satoshis or a small token, to your wallet. These small transactions are called “dust”. The attacker then monitors what you do with that dust, hoping you combine it with your real funds. This can reveal links between wallets and compromise your privacy. Dusting is often the first step in a larger phishing or social engineering scheme.
Dusting alone doesn’t give anyone access to your wallet or private keys. The funds they send are harmless if left untouched. However, interacting with dust, like spending it, consolidating it, or clicking links tied to it, can expose you to risk. Scammers may use your activity as a signal that your wallet is active, then follow up with phishing attempts or social engineering. So while the attack itself isn’t directly harmful, what comes after it can be.
The best action is not to touch the dust received in the wallet. Avoid including the dust in any outgoing transactions, don’t try to send it back, and never click on anything linked to it. If you're worried, move your actual funds to a new, clean wallet, being careful not to include the dust or any suspicious tokens. Also, monitor your wallet for unusual activity and stay alert for scam messages. Leaving the dust alone and isolating your funds is the safest route.
Start by using wallets that support dust filtering or coin control—these can hide small, suspicious amounts or let you manually choose what to include in transactions. Keep your wallets separated based on their purpose (e.g., trading, saving, interacting with dApps) so that if one gets dusted, your whole crypto presence isn’t exposed. Turn off auto-display features in wallets like MetaMask to avoid accidentally interacting with fake tokens. And always verify unknown transactions through a blockchain explorer before taking action. These habits go a long way in keeping your wallet private and safe.
In most places, dusting itself isn’t illegal. Sending a minor amount of cryptocurrency is not against the law, particularly on public, permissionless blockchains. When it's part of a larger fraudulent process, such as phishing, extortion, or identity theft, then it becomes part of an overall criminal process. Even certain businesses utilize dusting methods for data monitoring or advertising, which is probably legal but also very invasive. Whatever the intent, it always remains a red flag and should always be approached with caution.