
- Crypto
- July 22, 2025
Stolen data has become more than just a tool for identity theft. It’s a developing underground market where personal and financial information is traded daily. The dark web is where this illicit exchange happens, and it fuels scams in industries like crypto and forex.
Scammers don’t engage in time-consuming, targeted attacks on individuals. Instead, they capitalize on large volumes of leaked information, quickly acquiring whatever data they can access and using it to launch mass-targeted scams.
What’s particularly alarming is that many victims remain unaware their data has been compromised, often until it’s too late. By the time signs of fraud emerge, funds may have already been drained, or accounts could have been accessed and manipulated.
A significant portion of this stolen data circulates in underground online markets, fueling much of the cybercrime. Understanding how these markets operate gives individuals a crucial advantage in protecting themselves from becoming victims.
What is for Sale on the Dark Web?
The dark web is filled with illegal marketplaces. They work like normal e-commerce sites, but the products are far from legal. What’s available includes:
- Personal identity data: Full names, birthdates, phone numbers, email addresses, and even Social Security numbers are all up for grabs. Scammers use this info to open fake accounts, slip past ID checks, or pull off more convincing social engineering tricks.
- Financial information: Bank details, credit card numbers, PIN codes, and login credentials to online banking platforms are commonly sold. With that kind of access, fraudsters don’t need much time; they can move money, drain accounts, or run up charges before anyone notices.
- Login credentials: Hacked credentials for email, e-commerce, social media, and cloud storage accounts are sold in bulk. These are used for account takeovers, sending phishing links, or demanding ransoms after locking users out.
- Full identity packages (Fullz): These packages usually contain everything needed to pass Know Your Customer (KYC) checks. A typical Fullz may include a government-issued ID, selfies, utility bills, and a signature. They’re highly valuable for creating fake investment profiles or bank accounts.
- Medical records and insurance information: Health insurance IDs and patient data are also for sale. These can be used for medical fraud or filing false insurance claims.
- Social media and influencer accounts: High-follower accounts are sometimes hacked and sold. These accounts can then be used to push crypto scams or promote fraudulent forex platforms.
Everything is priced based on freshness, accuracy, region, and type of data. Newer, verified data is more expensive. A U.S. bank account with a verified balance could be sold for thousands or even millions of dollars.
How Do Fraudsters Find Their Victims?
Fraudsters don’t handpick individuals; they operate at scale. Once they buy a large batch of data, they use automated tools to sort through it.
They filter based on financial potential. Tools scan for salary data, investment history, and transaction volumes to locate people with more money.
Email patterns are also checked. A person using emails with financial service domains may be flagged as a potential investor.
Some scammers buy access to recent breach data, giving them highly relevant and recent contact lists.
Moreover, phishing kits play a key role. These kits create fake websites that mimic banking, exchange, or government portals. When a victim enters their data, it’s harvested and resold or reused immediately.
Once they identify the right targets, they begin their campaigns, often with personalized phishing messages, fake calls, or even social media outreach.
How the Dark Web Makes Stolen Data Accessible to Anyone?
One doesn’t have to be an expert to buy stolen data. That’s what makes the dark web so dangerous. The whole ecosystem is built for convenience. There are different ways where dark web makes stolen data accessible to anyone:
- Marketplaces: Marketplaces often have clean user interfaces, where you can search by country, bank, or even income level. Payment is mostly in crypto, which adds another layer of anonymity.
- Vendor Profiles: Vendor profiles show ratings, reviews, delivery guarantees, and even customer service contact options. You can even open a dispute if your purchase isn’t as promised.
- Subscription Services: Some platforms have a subscription model. Members pay a monthly fee to access fresh breach data, new phishing tools, or up-to-date Fullz packs. Forums and chat rooms offer tutorials. New scammers can learn how to use the data effectively or run scams without prior experience.
All this combined makes stolen data accessible to almost anyone, even someone with no background in hacking or fraud.
The Role of Stolen Data in Crypto and Forex Fraud Schemes
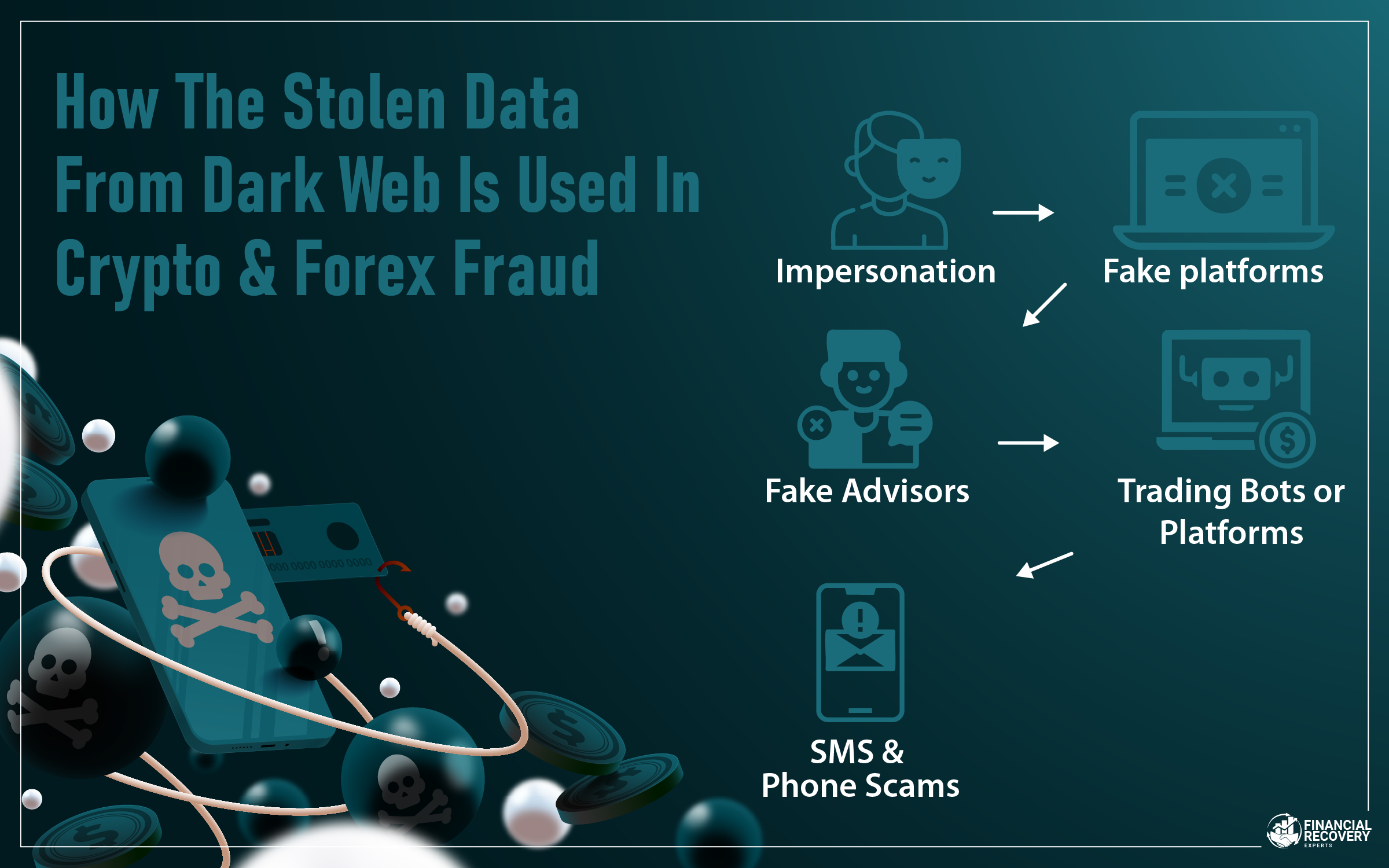
Crypto and forex frauds rely on illusion. And stolen data helps create that illusion. It makes scams more believable and more effective.
Impersonation: Scammers may pretend to be customer support from a known crypto platform. If they have your name and last transaction, it becomes convincing.
Fake platforms: They can create websites that look exactly like real investment portals. Using stolen data, they pre-fill forms to gain your trust. You think you're seeing your own records.
Fake advisors: Some scams involve fake financial advisors reaching out via LinkedIn or email. They use your job title and company data to tailor their message, offering "personalized" investment advice.
Trading bots or platforms: They may use your identity to simulate real users on fake platforms. These fake platforms show fake profits, encouraging others to join.
SMS and phone scams: With your mobile number, they can send timed SMS links pretending to be urgent investment opportunities. Clicking them often leads to credential theft or malware installation.
In essence, your data helps build a false reality, one in which you're more likely to trust, click, and invest.
The Financial Impact on Victims
Falling victim to these scams can lead to more than just an empty wallet. The consequences ripple through a person's financial and emotional life.
Money drained from accounts: Once fraudsters get in, they act quickly. Within minutes, they might transfer out your savings, max out credit cards, or convert money into crypto to make it harder to trace.
Loans taken in your name: Using full identity details, scammers may apply for loans or open credit lines. Victims are then left to deal with debt collectors, ruined credit, and drawn-out disputes.
Lost investments: Many people who fall for fake crypto or forex schemes end up wiring money or buying digital currency to transfer. These funds are nearly impossible to recover.
Credit score damage: When unauthorized loans or transactions go unpaid, credit bureaus record that activity. Even if you prove it wasn’t your fault, it takes time and effort to repair the damage.
Legal headaches: Sometimes it goes beyond just money. If your name is associated with fraud or illegal transactions, you may be flagged for issues such as tax evasion or money laundering. Getting out of that mess can mean lawyers, calls, forms, and a whole lot of stress.
Mental toll: The stress of being scammed affects sleep, confidence, and peace of mind. People feel violated and often blame themselves, even though the real fault lies with the scammers.
How to Protect Yourself from Dark Web Data Theft?

You can’t stop every leak. But there are a few things you can do to make yourself a harder target. Scammers usually go for the easy ones. Don’t make it easy for them:
Don’t reuse passwords: If one site gets hit, they try those same login details everywhere. That’s how they break into your email, bank, or trading app. Using different passwords for every account helps block that chain reaction. If remembering all of them is a pain, use a password manager.
Use two-step verification: It adds a second layer, usually a code sent to your phone. Even if someone steals your password, they still can’t get in without that code. It’s a small step that stops a lot of attacks.
Keep your devices updated: Outdated apps and software are full of holes. That’s how hackers sneak in. Update and patch those holes. Don’t put them off.
Don’t trust weird links: If you get a random message telling you to click something right now, stop. Go to the real website yourself. Scammers love urgency; it’s how they rush you into bad decisions.
Watch your accounts: Check your bank and credit card statements often. Look for stuff you don’t recognize. Keep an eye on your credit report, too. Sometimes it’s the only way to spot someone messing with your info.
Be careful what you share: Posting your birthday, job title, or vacation plans might seem harmless. But scammers piece that together. It makes their lies more convincing later.
None of this guarantees you’ll stay safe. But it can slow scammers down, and that’s often enough to make them move on to someone else.
How Authorities Are Combating the Data Economy of Dark Web?
Cracking down on the dark web isn’t easy, but global efforts are picking up speed. Governments, agencies, and cybercrime units aren’t working in silos anymore, they’re teaming up.
- Cross-border teamwork: Countries are sharing intel, combining tools, and running joint operations to unmask the people running dark web markets. No single agency can do it alone, so this kind of collaboration matters.
- Following the money: Crypto used to be seen as untraceable. Not anymore. Investigators now use blockchain-tracking tools to follow transactions and connect digital wallets back to real people. It’s technical, but it’s working.
- Taking sites down: Some of the biggest dark web markets have been shut down in recent years. When those sites disappear, it throws scammers into chaos. They lose tools, vendors, and trust all at once.
- Targeting the operators: Law enforcement isn’t just going after low-level users. They're focusing on developers, moderators, and sellers, the ones keeping these networks alive. When they fall, a lot of the system falls with them.
- Spreading the word: Authorities aren’t just fighting crime in the background; they’re also warning the public. Awareness campaigns help regular people spot scams before they get caught up in them.
For every dark web marketplace that gets shut down, another one seems to emerge in its place. It’s a never-ending cycle, and it’s exactly why you should stay alert and aware.
The Growing Threat of Data Exploitation Beyond the Dark Web
The problem isn’t limited to the dark web anymore. Stolen data spreads through:
Telegram and WhatsApp groups: Private channels exist solely for data trading. Fraudsters coordinate scams, share targets, and sell fresh dumps.
Public forums and marketplaces: Some surface web platforms, disguised as marketing or research sites, provide access to low-cost stolen data.
Insider leaks: Employees at small companies sometimes sell customer data to dark web resellers. This insider threat is growing.
AI-driven phishing: Bots now use AI to create convincing fake messages. Combined with stolen data, these bots run scams automatically.
Data laundering: Some companies purchase stolen data, clean it, and resell it as "market research." This legal gray area spreads the data further.
Data no longer needs the dark web to be misused. It’s becoming a broader digital threat.
Is visiting the dark web against the law? No, simply browsing the dark web isn’t illegal in most countries. The problems start when people access, buy, or share illegal content like stolen personal data
FAQs (Frequently Asked Questions)
You might not. A lot of people only find out after the fact, like weird charges, strange emails, that kind of thing. Some apps can flag when your email’s in a breach, but it’s not always instant or complete. It’s more of a heads-up than a guarantee.
No. Once it's leaked, it's out. The best move is to Change passwords, watch your accounts, maybe freeze your credit if things look sketchy. You’re mostly trying to stop more damage at that point.
Not always. Some are just spammy links or fake accounts sliding into DMs. But a lot of them use info from the dark web to make it feel real. That’s the scary part—they know just enough to sound convincing.
Yes. Even if one spotted it and shut it down fast, their report helps. Law enforcement needs that information. It shows patterns, helps them connect dots. Plus, it warns others. Every bit helps.
You can lower the odds, sure, but totally stopping it? That’s tough. Stuff leaks all the time. What you can do is use good passwords, 2FA, be picky about what you share. Doesn’t make you bulletproof, but it puts up walls.